Introduction
- • Symmetric Key (Secret Key Cryptography): Uses a single key to encrypt and decrypt the messages
- • Asymmetric Key (Public Key Cryptography): Uses one key to encrypt and another key to decrypt the messages
- • Hash Functions: Uses a mathematical transformation that transforms the message into a fixed length data that is unique to the corresponding source.
- • Data Encryption Standard (DES)
- • Advanced Encryption Standard (AES)
- • Rivets Cipher (RC)
- • International Data Encryption Algorithm (IDEA)
- • Blow-fish
- Distribution of key – Secret key sharing among senders and receivers. If there are n parties- involved in the communication then n(n-1) keys to be distributed. Managing this many keys is another problem.
- Authenticity – Trust and Authenticity of two parties.
- • Diffie Hellman
- • RSA (Rivest, Shamir, Adleman)
- • Digital Signature Algorithm (David Kravitz)
The RSA keys are derived from a variable size encryption block and a variable size key. The key-pair (public and private) is derived from a very large prime number, chosen according to special rules. The strength of RSA depends on the key length but choosing a long key can slow down the system. For bulk data encryption, it is recommended to use DES for better performance.
- The message has to be first encrypted using the private key of the sender.
- • The encrypted message is then encrypted using the public key of the receiver.
- • The encrypted message is sent to the receiver.
- • The receiver on receiving the encrypted message decrypts it using his (receiver’s) private key.
- • The semi-decrypted message is then decrypted using the public key of the sender.
- • The receiver obtains the plain text message.
- • No need to exchange the keys
- • Another key cannot be derived from one key
- • The confidentiality of the message can be ensured by using the public key cryptography
- • It is possible to establish authentication of the sender by using public key cryptography
- (digital signature)
- • It is possible to ensure the confidentiality and authentication of the message at the same time
- • It is possible to use public key cryptography for session key exchange
- • Digitally signed document
- • E-mail encryption software such as PGP and MIME
- • RFC 3161 authenticated timestamps
- • Digital signatures in the Operating System software such as Ubuntu, Red Hat Linux packages distribution
- • SSL protocol
- • SSH protocol
A public key infrastructure consists of:
- A Certificate Authority (CA) that issues and verifies digital certificates. A certificate includes the public key or information about public key
- • A registration Authority (RA) which verifies the user’s authenticity for CA before CA issues a digital certificate
- • A secured storage place to hold the certificates and public keys
- • A certificate management system
- • Hardware, software, policies, procedures, and people used to create, manage, and revoke digital certificates along with the distribution and storage of the digital certificates
A certificate contains information referring to a public key, issued by a Certification Authority (CA). The information in the certificate should conform to the ITU (IETF) standard X.509 v3. Certificates conforming to that standard include information about the published identity of the owner of the corresponding public key, the key length, the algorithm used, associated hashing algorithm, dates of validity of the certificate, and the actions the key can be used for.
Certificate Authority (CA)
A CA is responsible for issuing certificates. CA issues the digital certificate based on the recommendation of RA. This digital certificate is signed by the CA using its own private key. The CA issues the certificate which contains the public key of the party who owns the certificate. Certificates have to be purchased from the CA. CA can issue a certificate only after it confirms all the credentials to prove your identity. Once identity is proved, it stamps the certificate to prevent modifications of the details contained in the certificate. CA is analogous to a passport agency. An individual or organization may have any number of certificates issued by different CAs. Different web applications may insist to use a particular certificate. For example, a particular bank may insist to use a certificate issued by that bank for a secured transaction, whereas some other web site may accept any certificate issued by any CA. Registration Authority (RA) is a third-party verification agency for a Certificate Authority (CA), to perform the verification of the organization or individuals who have applied for the certificate. Final component of the PKI is the Certificate Management System (CMS) through which certificates are published, renewed, or revoked. Examples of Certificate Authority (CA) include Verisign, Thawte, SSL.com, RapidSSL, Network Solutions, GlobalSign, Digicert, Enutrust.net, PinkRoccade, and PKI.CAcert. 24
Digital Certificate
Digital Certificate provides an electronic identity to conduct secure transactions by providing your identity (authentication). It is similar to a passport or driver’s license. With a digital certificate, an organization or an individual can provide authentication for all the transactions with friends, business partners, and other online services. Digital certificate assures identity among all the parties involved in the transactions. The most widely used format of a digital certificate is as defined by the CCITT X.509 standards. 25 Digital certificate uses public key cryptography to verify the integrity of the certificate itself.
Hash Function Cryptography
Hash functions, also called message digests, use a fixed length hash value to transform the data that makes it difficult for someone to decry-pt or change the data without affecting the hash value, thus securing the data from intruders. Hashing functions are one-way mathematical functions that are easy to compute but hard to reverse. A hash function H( ), applied on input (x), and returns a fixed string, hs. Mathematically it is written as hs = H(x). A cryptographic hash function in general should have the following properties:
- • Flexible input length (x)
- • H(x) should be relatively easy to compute
- • H(x) is one way function and cannot be reversible
- • The output is of fixed length and does not depend on input length
Hashing is generally used in the following situations:
- • Password management in case of PPP, CHAP, and Microsoft EAP. This method of cryptography is normally used in operating systems to protect passwords.
- • Digital signatures and file integrity checkers to check the integrity of data.
Hashing functions are used to vouch for the integrity of the message by appending the message with the hash value. If the message is changed, the hash value when recomputed will not match the pre-computed hash value. In order to avoid man-in-the middle attacks, it is ideal to send the hash value in a secure way to the intended party. Such secure transfer is possible using public key cryptography. Further, hash value is used to store passwords of the operating systems like Microsoft Windows. Here, the original passwords are not stored; instead the SAM corresponding hash values are stored. These provide high security to the passwords, as hash value is not reversible to find out the original password. Only when the passwords are entered in the system will it compute the hash value and check with the hash value stored in the SAM. “Salting” the password before hashing by either suffixing or prefixing it with a random string decreases the possibility of cracking the password. Hashing is also used in some of the implementation of digital signatures which vouches for the integrity of the message sent. Hashing functions are also used in virus detection as well as intrusion detection.
Figure 10-8 illustrates how hashing ensures the integrity of the message that is sent.
Popular Hashes
MD5 (Message Digest Function 5), SHA1 (Secure Hash Algorithm 1), SHA2 (Secure Hash Algorithm 2), and SHA3 (Secure Hash Algorithm 3) are the popular hashing functions /algorithms. MD5 outputs are of 128 bits and are popularly used for storing of the passwords as well as to ensure file integrity. MD5 is prone for collision. SHA algorithms again provide for one way hash. SHA1 provides for 160 bit output. SHA-224, SHA-256, SHA-384, and SHA-512 are known as SHA-2. SHA3 is the most advanced hashing function which was announced by NIST in 2012. SHA-3 has a unique structure known as sponge construction. MAC (Message Authentication Code) is another popular hash function which is also known as a Keyed Hash Function.
Digital Signatures
A digital signature is like a handwritten signature but it is in the digital form for an electronic document. The document containing the digital signature is verified by the recipient using a hash function to check whether the message has been altered either intentionally or accidentally during the transmission. If the message is altered, the hash function returns a different result. Digital signature ensures authenticity and non-repudiation. Here, usually the hash value is encrypted with the sender’s private key. This provides for the authenticity. When the receiver decrypts the private key using the sender’s public key, he gets the hash value. He can check this hash value with the hash value generated using the hash algorithm from the message received. Alternatively, both the message and the appended hash value both can be encrypted with the sender’s private key in a similar way as above. If both the hash value received and the hash value generated from the message received tally that means the integrity of the message is maintained. Because it has been signed by the sender’s private key, the message sender is also authenticated. Another alternative is to encrypt the message and the hash value using the symmetric key shared between both the parties.
Summary of Cryptography Standard Algorithms
Table 8-2 summarizes some of the Symmetric cryptographic algorithms that are used today.
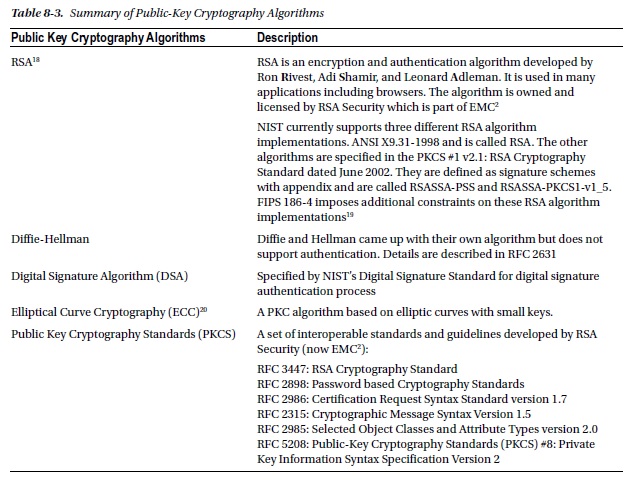
Table 8-3 summarizes the Public-Key Cryptography Algorithms that are commonly used today.
Table 8-4 summarizes some of the Hash function algorithms that are commonly used.
Each of the algorithms in Table 8-4 is used in different applications and for different purposes. For example, Hash function algorithms are well suited for data integrity. Any change made to the content during the transmission will result in a hash value different from the original value sent by the sender. Since it is highly unlikely that the same hash value is generated for two different messages, data integrity is ensured. Symmetric key cryptography is suited for encrypting and decrypting messages, thus providing privacy and confidentiality. The sender can generate a key for each data session to encrypt the message and the receiver can decrypt the message but needs to have the same key for the same session. Symmetric key cryptography also may be used for file encryptions. Public Key cryptography technique uses a pair of keys called private and public. This is used for not only confidentiality of message but also for non-repudiation and user authentication. Table 8-4 provided an overview of different algorithms used for different types of cryptography techniques. Table 8-5 provides an overview of some of the common cryptographic algorithms that are used in various applications, particularly in e-commerce applications.
Disk / Drive Encryption
With the increased use of the mobile devices like laptops and the storage of confidential data on their hard disk and data carried on USB and other drives, we need to protect the data from theft and misuse. Hence, the disk encryption utilities have emerged. The entire hard disk, USB drive, and other drives can be encrypted so that the data on them cannot be read and misused by unauthorized persons. Now, we have the possibility to burn the data on to portable disks but encrypt them so that unauthorized persons will not be able to misuse them. The utilities and tools such as TrueCrypt and Gilisoft are widely used for disk encryption, and are found to be very effective in disk encryption. There are many other tools available such as DriveCrypt, DiskCryptor, Rohos Disk Encryption, and Symantec Drive Encryption.
Attacks on Cryptography
There are various attacks possible on cryptography. Some of the common attacks are:
- Rubber Hose Attack: Obtaining by force the secret key like password to the file from those who have them
- • Cipher-text-only Attack: Here the attacker has the cipher-text and tries to get the encryption key using the cipher-text
- • Known-plain-text Attack: Here the attacker has some plain-text. Using this he tries to get the encryption key
- • Chosen-plain-text Attack: Here the attacker uses his own plain-text. He then encrypts them and analyses the resulting output, i.e., cipher-text.
- • Adaptive Chosen-plain-text Attack: Here the attacker uses various plain-texts. The subsequent plain-text will be used by him based on the result of earlier output.
Brute force and Frequency Analysis methods are popularly used by the attackers to break the encryption key.
What is Cryptography?
Cryptography is the science of secure communication in the presence of third parties, often referred to as adversaries. It enables individuals to securely transmit and store information such that only the intended recipient can access it. Cryptography achieves this by employing various techniques to encode information, making it unreadable to anyone without the proper decryption key.
Basic Concepts in Cryptography:
Encryption: Encryption is the process of converting plaintext (normal, readable data) into ciphertext (encrypted, unreadable data) using an encryption algorithm and a secret key.
- Decryption: Decryption is the process of converting ciphertext back into plaintext using a decryption algorithm and the corresponding secret key.
Key: A key is a piece of information used in conjunction with an encryption algorithm to transform plaintext into ciphertext and vice versa. Keys can be either symmetric or asymmetric.
Symmetric Cryptography: In symmetric cryptography, the same key is used for both encryption and decryption. This means that both the sender and the receiver must have access to the same secret key.
Asymmetric Cryptography: In asymmetric cryptography, also known as public-key cryptography, each participant has a pair of keys: a public key and a private key. The public key is used for encryption, while the private key is used for decryption.
Now, let's illustrate these concepts with some diagrams:
Diagram 1: Symmetric Cryptography
lua +-------------------+
| Plaintext |
+-------------------+
|
v
+-------------------+
| Encryption |
+-------------------+
|
v
+---------------------+
| Ciphertext |
+---------------------+
|
v
+---------------------+
| Transmission |
+---------------------+
|
v
+---------------------+
| Reception |
+---------------------+
|
v
+---------------------+
| Decryption |
+---------------------+
|
v
+-------------------+
| Plaintext |
+-------------------+
Diagram 2: Asymmetric Cryptography
lua +-----------------------+
| Plaintext |
+-----------------------+
|
v
+-----------------------+
| Encryption |
+-----------------------+
|
v
+-------------------------------------------+
| Transmission of Encrypted Message (Ciphertext) |
+-------------------------------------------+
|
v
+-------------------------------------------+
| Reception of Ciphertext |
+-------------------------------------------+
|
v
+-----------------------+
| Decryption |
+-----------------------+
|
v
+-----------------------+
| Plaintext |
+-----------------------+
These diagrams illustrate the basic processes of encryption and decryption in both symmetric and asymmetric cryptography. In symmetric cryptography, the same key is used for both encryption and decryption, while in asymmetric cryptography, different keys are used for encryption and decryption.






















No comments:
Post a Comment